Setting up Damn Vulnerable Web Application (DVWA)
02 Apr 2017
.
tech
.
Comments
#security
#redteam
#dvwa
Damn Vulnerable Web Application (DVWA) is a purposely insecure PHP/MySQL web application created for security professionals, web developers, students, and teachers to learn about web application security in a controlled environment. The application is intended to help security enthusiasts test their skills and tools in a legal setting and help web developers understand the process of securing web applications. DVWA is designed to provide a simple and straightforward interface to practice some of the most common web vulnerabilities at various difficulty levels. It contains both documented and undocumented vulnerabilities, which encourages users to identify as many issues as possible.
To get started with DVWA, download the source code from GitHub and set up the environment on Kali Linux, in order to have most of the tools you’ll need preinstalled. DVWA requires Apache and MySQL, which are already installed on Kali Linux as well.
Download and unzip DVWA:
wget https://github.com/ethicalhack3r/DVWA/archive/master.zip -O dvwa.zip
unzip dvwa.zip
Start Apache and MySQL:
service apache2 start
service mysql start
Move DVWA to /var/www/html and setup permissions:
mv DVWA-master /var/www/html/dvwa
cd /var/www/html
chmod -R 755 dvwa/
After completing the setup, update your MySQL password in the DVWA configuration
file to create the dvwa database:
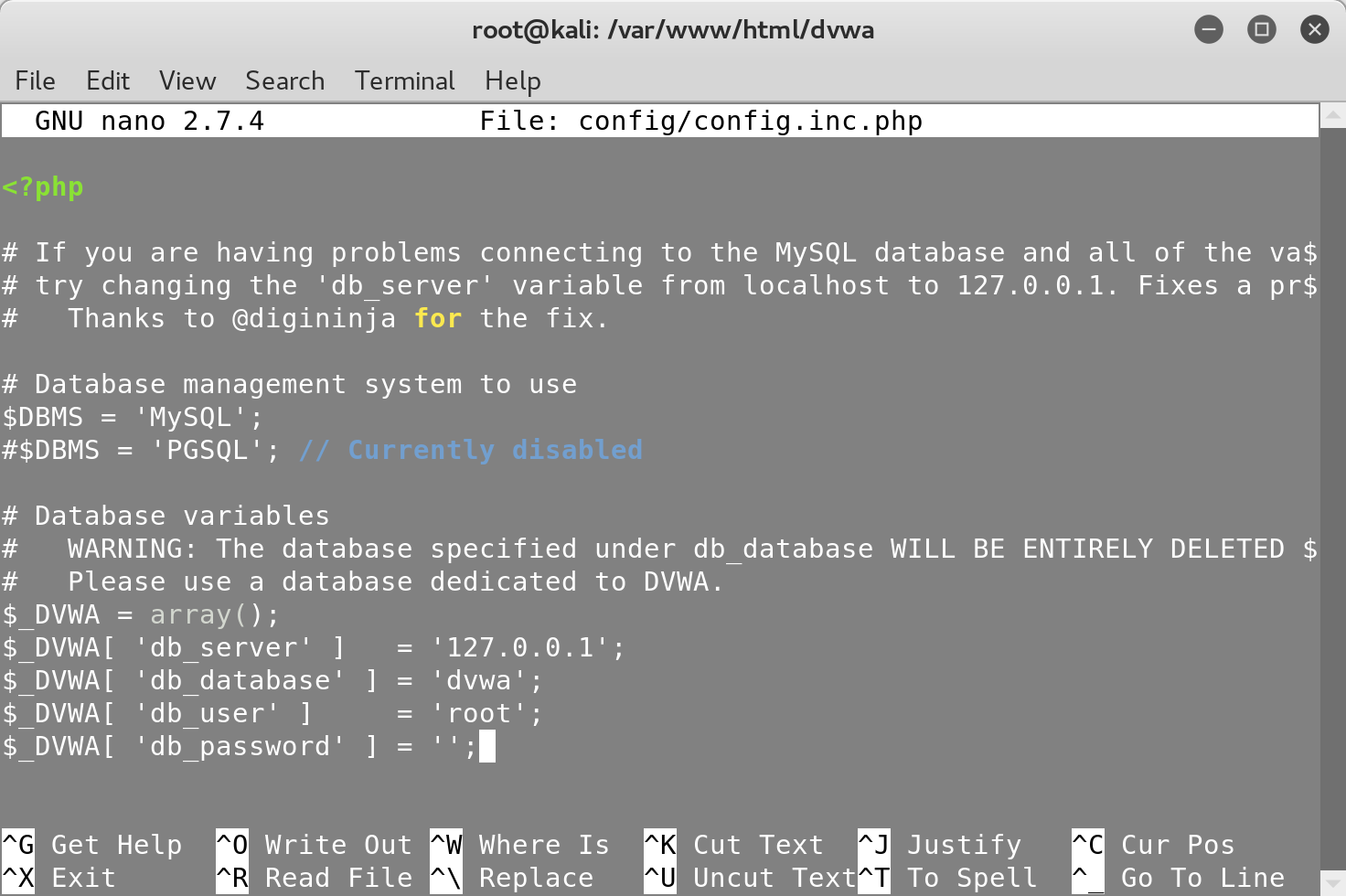
You can then access the login page by visiting http://127.0.0.1/dvwa. Make
sure to set the security level of DVWA to low under the ‘DVWA Security’ tab to
begin exploring the low-hanging fruits of web vulnerabilities:
Note that you should never expose this web application in a non-private network
and always reset the security level to impossible.
In the next post we’ll exploit the first vulnerability of DVWA in order to login to the application without knowing the password.
